There’s a monumental shift taking place in the digital economy. Like any growing platform, DDoS attacks are real, silent threats that must be dealt with at the highest grade of concern.
Our API typically receives over 1M+ requests every day, processing requests from over 142 different countries. We saw over 33.6M+ requests in the past month, with 135.22GB+ being transferred.
We consistently receive over 3.9M+ daily requests (verified and coming from real users) from 200+ different countries. For the past 30 days, we’ve seen over 351.27M+ requests with 8.02TB+ transferred, as noted in our first annual security report we published last month.
Security threats are a regular occurrence from 1 AM to 12 AM on our global infrastructure. These threats are led by competitors and bad actors with ill intent.
214.10K
The number of requests per second of the largest DDoS attack we have ever received, as documented in our annual security report, translates into:
- 12.84M requests per minute
- 308.30M requests in an hour
- 7.39B requests in a day
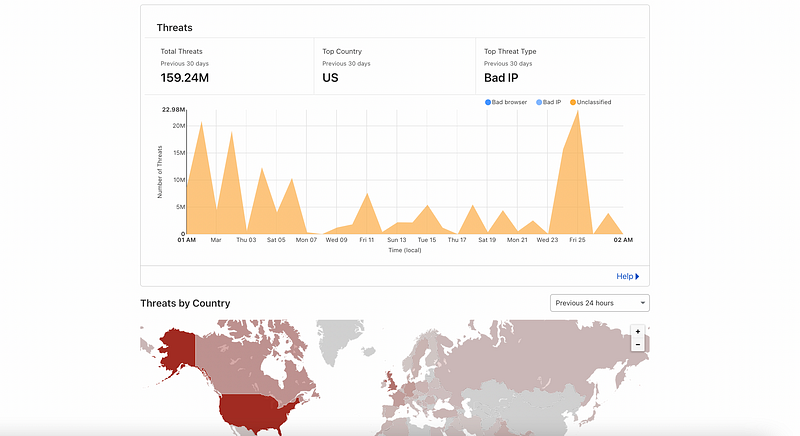
We continue to be a target of Layer 7 DDoS attacks every day with over 159.24M+ security threats over the past 30 days:
- Indonesia with 3.80M+ requests
- China with 2.40M+ requests
- Russian Federation with 2.30M+ requests
- India with 2.24M+ requests
- United States with 2.06M+ requests
These Layer 7 DDoS attacks targeted our domain directly (sellix.io:443/) and not any of our business customers’ domains or subdomains. We’ve made a more considerable investment to mitigate DDoS attacks, and we’ve been able to do so with immeasurable success.
A deeper dive into the situation
As a SaaS eCommerce platform, Sellix provides the infrastructure and logic for hundreds of thousands of merchants worldwide to create, sell and commerce their digital goods.
As a platform, we don’t only have to worry about our competitors, which seem to rely on DDoS attacks rather than improving their websites: we also have to worry about every competitor and antagonist of our merchants.
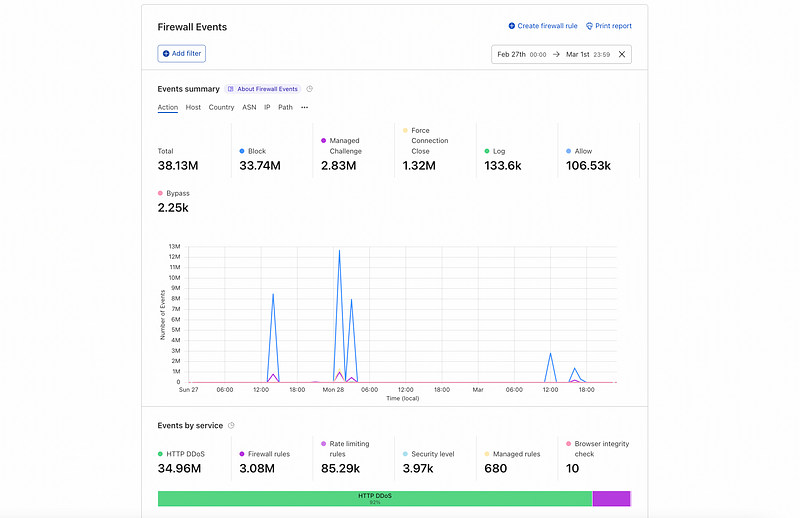
This results in frequent DDoS attacks, daily even that account for over 159.24M threats in the past 30 days and around 27.15M requests blocked every day by our WAF.
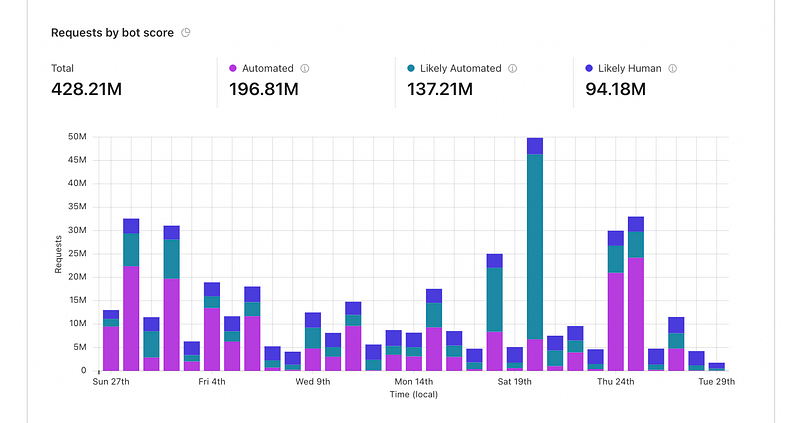
DDoS attacks can be grouped into BOT requests; as seen from the image above, we received over 334M requests that were likely or almost certain to be automated in the past 30 days.
The increasing growth
As unfortunate as it sounds, the situation is not getting better. Just a year ago, we were not experiencing half as many attacks as we are now, with less than 1/10 of the rps (requests per second) used in today’s attacks.
How we have tackled the situation
In this case, like many others, being on the cloud helps:
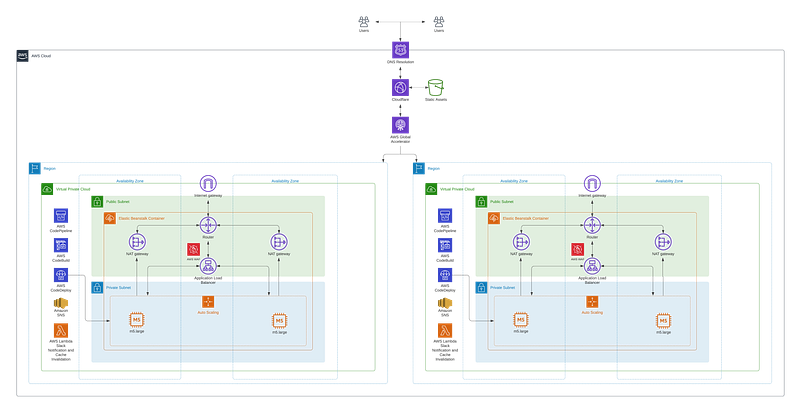
Our AWS infrastructure automatically scales with the increasing traffic that we receive. However, that is not nearly enough, as large DDoS attacks can saturate tens of servers, no matter their size.
This is where Cloudflare comes in. Thanks to their solution, which we have explicitly configured for our use case with their team, we filtered out almost 100% of the bad traffic into our cloud infrastructure and reduced downtimes near to zero, as can be seen on our status page.
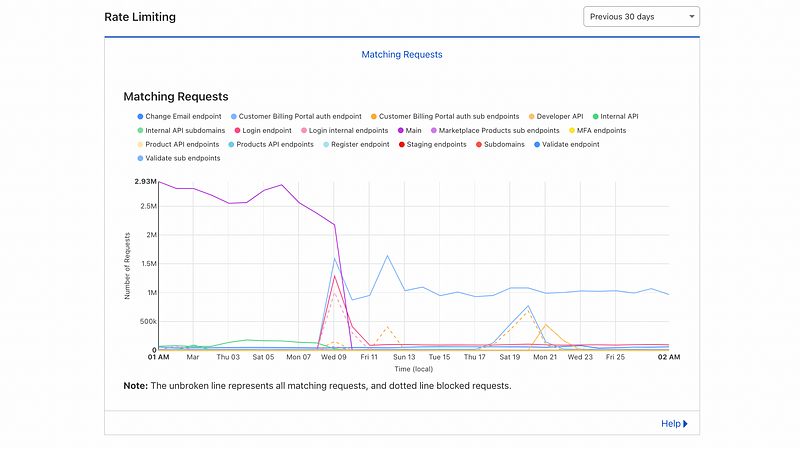
Rate-limiting
Simple, yet effective. Rate-limiting is one of the best ways to lock down specific API endpoints and website pages.
The infrastructure of our web solution is documented on our GitHub repository, featuring every AWS service we use under Cloudflare as a CDN.




